Since seventies, computer networking is growing exponentially and has become an indispensable part of everyone’s life owing to its applications in varied commercial sectors including private and government like schools, banks, hospitals, military organisations, and even homes. However, it is extremely confusing for a beginner due to lack of consistency in networking standards and its terminology. Hence, to excel in networking, it is imperative to dig deeper and understand the five key aspects as such:
1.
Internet applications and network programming.
2.
Data communications.
3.
Packet Switching and networking technologies.
4.
Internet working with TCP/IP.
5.
Additional networking concepts and technologies.
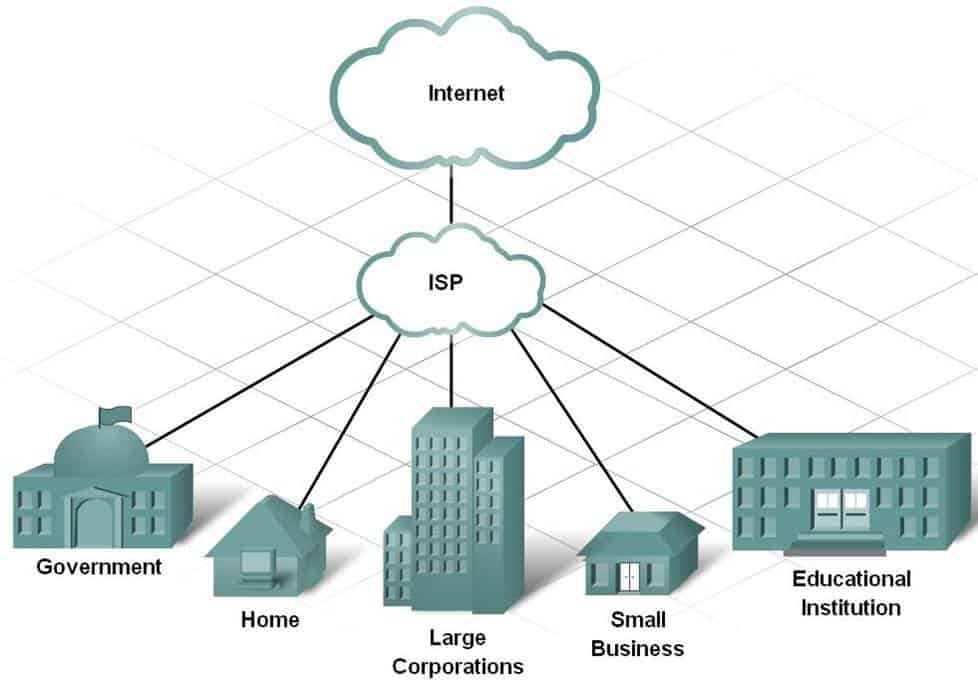

Understanding Network Programming/ Networking:
Internet offers distinct applications for the convenience of end users offering well defined protocols. Along with this, it also offers various network services like naming, configuring, filing and printing servers. All internet applications work on single transport layer that provides TCP and UDP and Network layer providing IP and port numbers ( System, User and Dynamic) to create a possible communication channel between them. There are two main paradigms for writing Internet applications that is client server and Peer-to-Peer(P2P).
Network programming involves writing computer programs enabling communication between different devices connected across a computer network whether its connection oriented or connection-less. Traditionally network planning includes seven different layers of OSI/ISO model as below:
 |
| OSI Model |
** TCP: Transmission Control Protocol: Connection Oriented communication that allows reliable communication between two applications.
**UDP: User Data-gram Protocol: Connection-less Communication that allows transfer of packet data between two applications.
**IP: Internet Protocol: Label or address assigned to each device connected with the computer.
**OSI/ISO: Open Systems Interconnection: Model showing the communication of applications over a network.
Network Hardware Components:
For planning, troubleshooting and maintenance of networks some devices are generally used like Servers, Routers, Repeaters, Hubs, Switches, Bridges, Gateways and many more.
1. Servers: Performs network functions for the computers and have several categories:
- File and Print Servers
- Application servers
- E-Mail servers
- Networking servers
- Internet servers
- Remote Access servers
2. Routers: A device that allows transfer of data in the form of packets from one network to another. Basically, it is used to provide broadband internet connection either to a PC or LAN in an organisation. They also contain RJ 45 Ports to connect other network devices using network cables.
3. Repeaters: Repeaters acts as a signal boosters that re-generates signals and allows transmission of them at a longer distance.
4. Hubs: Consists of several Input and Output ports and can splits the same network signals into all connected computers. It also acts as a multi port repeater.
5. Switches: It is an advanced version of a hub and uses physical address to send the signal only to the destination port instead of broadcasting it.
6. Bridges: It connects two separate Ethernet network (following same protocol) together and establish a connection between them by forwarding packets from one port to the destination port.
7.Gateways: It acts as a gate that allows entrance of a signal in a network and can connect entirely different networks (following different protocols) together to allow transfer of signals.
3. Repeaters: Repeaters acts as a signal boosters that re-generates signals and allows transmission of them at a longer distance.
4. Hubs: Consists of several Input and Output ports and can splits the same network signals into all connected computers. It also acts as a multi port repeater.
5. Switches: It is an advanced version of a hub and uses physical address to send the signal only to the destination port instead of broadcasting it.
6. Bridges: It connects two separate Ethernet network (following same protocol) together and establish a connection between them by forwarding packets from one port to the destination port.
7.Gateways: It acts as a gate that allows entrance of a signal in a network and can connect entirely different networks (following different protocols) together to allow transfer of signals.
 |
| Network Hardware Devices |
Network Cables:
Out of the various network cables available in the market, the most common used cable for LAN's is Category 5 (Cat-5) or Category 6 (Cat-6) which is a twisted pair cable and allows the network signal to travel through eight wires in total (four twisted pairs), and follows different arrangements and color coding to transfer different signals through Ethernet cables.
 |
| CAT5 Cable |
1. Standard or Straight: Here both the ends of the cable follows same colour coding or wiring pattern as below:
RJ45
Pin#
|
Wire
Color
|
10/100
Base-T Use
|
1
|
White/Orange
|
Transmit +
|
2
|
Orange
|
Transmit
-
|
3
|
White/Green
|
Receive +
|
4
|
Blue
|
Unused
|
5
|
White/Blue
|
Unused
|
6
|
Green
|
Receive
-
|
7
|
White/Brown
|
Unused
|
8
|
Brown
|
Unused
|
2. Crossover: Here the arrangement of both the ends are different from each other as below:
RJ45Pin#(END1)
|
Wire Color(END1)
|
RJ45 Pin#(END2)
|
Wire Color(END2)
|
1
|
White/Orange
|
1
|
White/Green
|
2
|
Orange
|
2
|
Green
|
3
|
White/Green
|
3
|
White/Orange
|
4
|
Blue
|
4
|
White/Brown
|
5
|
White/Blue
|
5
|
Brown
|
6
|
Green
|
6
|
Orange
|
7
|
White/Brown
|
7
|
Blue
|
8
|
Brown
|
8
|
White/Blue
|
** LAN: Local Area Network: A computer network that allows communication between computers within a limited area.
**RJ45: Registered Jack 45: Standardized networking interface used for Ethernet cabling.
Understanding Cable Topologies:
Network Topologies or Network Architecture refers to the shape of the network. To clarify, it means the logical arrangement in which all the points (nodes) of a network are connected together via network wires. Network follows various topologies like Point to Point, Bus, Star, Ring, Tree, Mesh, Hybrid, their overview is as below:
**RJ45: Registered Jack 45: Standardized networking interface used for Ethernet cabling.
Understanding Cable Topologies:
Network Topologies or Network Architecture refers to the shape of the network. To clarify, it means the logical arrangement in which all the points (nodes) of a network are connected together via network wires. Network follows various topologies like Point to Point, Bus, Star, Ring, Tree, Mesh, Hybrid, their overview is as below:
S. No.
|
Topology
|
Definition
|
Advantages
|
Disadvantages
|
1
|
Point to point
|
Direct link between two computers
|
Faster and Reliable
|
Used only for small areas where computers
are in close proximity.
|
2
|
Bus
|
Uses one main cable to connect all
the computers or nodes
|
Easy to connect and cost effective
|
If one cable breaks the entire
network can broke down. Hence, it is difficult to troubleshoot.
|
3
|
Ring
|
Devices are connected in a circular
form indicating a ring.
|
Easy to install and configure and
detecting faults within a network.
|
It has unidirectional traffic and
break in a single ring can halt the entire network.
|
4
|
Star
|
Each computer is connected with a
hub at the center using point to point connection.
|
Problem with one node does not affect
other nodes.
|
More expensive, because it requires
more cables for connecting devices.
|
5
|
Tree
|
Elements are connected in an
arrangement similar to branches of the tree.
|
Expansion of nodes is easy, and the
network can be easily maintained, managed and diagnosed in case of any error.
|
If central hub is failed, then the
whole network will stop working. Maintenance is also difficult because it is
heavily cabled and hence, costly as well.
|
6
|
Mesh
|
All nodes cooperate with each other
to distribute data.
|
Traffic can be easily managed, and
failure of a device does not affect data or network flow.
|
Cost, building and maintenance of a
network is on high side.
|
7
|
Hybrid
|
Includes mixing of two or more
different network topologies.
|
Reliable having better fault
tolerance. Offers flexibility, hence, most effective.
|
 |
| Network Topology |
Networking Protocols:
A network protocol is a set of rules followed to establish a communication network and completing desired network transactions. Some commonly used network protocols are TCP/IP and UDP, DNS, DHCP, HTTP, FTP, SMTP, VoIP and so on.
1. TCP/IP and UDP: TCP/IP is basically two different protocols but generally used together in concert with each other. Here, the IP (Internet Protocol), not only defines the way to address network data from source to destination but also tells the correct sequence in which the data is re-assembled at the other end. It operates at the network layer in OSI model. Whereas, the TCP (Transmission control protocol) operates at Transport Layer. It mainly manages connections between computers.
However, the UDP (User Datagram Protocol) has almost similar roles as TCP but unlike TCP, it re-sends any un-received packet back and is faster and reliable for insignificant network communications.
2. DNS: Domain Name System: It is a naming system introduced for humans to access online information eliminating the need to remember complex IP addresses. Here, some domain names are assigned to various IP addresses to make it convenient for humans to access them.
3. DHCP: Dynamic Host Configuration Protocol: It basically deals with network management where the server assigns an IP address, default gateways and other network parameters to develop a communication between different networks.
4. HTTP: Hypertext Transfer Protocol: Protocol used by World Wide Web (WWW) to access hypertext documents including hyper text links can easily be accessible by the user through various web browsers like Google chrome, Mozilla Firefox, Microsoft Internet Explorer and so on.
5. FTP: File Transfer Protocol: It is an application layer protocol primarily used for sending and receiving files between a client and a server where transfers are generally text-based and password protected.
6. SMTP: Simple Mail Transfer Protocol: It is an application layer protocol used for sending and receiving E-mail messages between servers and is decoded at the receiver end by using one of POP (Post Office Protocol) or IMAP (Internet Message Access Protocol).
7. VoIP: Voice Over IP: It is a process of transmitting voice calls or messages over IP networks and allows us to make free or very less priced telephone calls over the internet.
Remote Network Access:
Allows users to access the system or a network through a network connection even if the person is not physically present at the site. To establish remote access connections different technologies are used as such:
1. Remote Node: A process in which a terminal or a computer system located far away from the main network can access LAN connection via an Internet or dial-up connection.
2. Remote Control: A process in which a remote user can take control of another workstation directly connected with LAN via some software installed on both the PCs. This also uses a dial-up line or an Internet connection.
 |
| Remote Control Session |
3.VPN: Virtual Private Networks: A link created between the remote user (Connected to ISP) and the company's LAN via Internet over a public network. It uses encrypted layered tunneling protocol that makes it a secure private network and often requires authentications to gain its access.
 |
| Typical VPN Connection |
Network Security:
It consists of set of rules, regulations and policies adopted to protect the integrity and prevent unauthorized access of a computer network peripherals either by hardware or software. Basically threats may be Internal, external or by viruses and other malicious software.
1.Internal Security: Refers to securing the network from internal threats like accessing unauthorized information by impersonating other users or deliberately introducing viruses to the network. Sometimes the users even sniff packets on the network to discover login in credentials of the company.
2. External Threats: Refers to securing network from external threats like Front-Door Threats, Back door Threats and Denial of Service (DoS).
**Front-Door Threats: It arises when an outsider cracks the password and access the network.
**Back-Door Threats: It arises when software or hardware bugs allow attacker to login the administrative account.
**Denial of service(DoS): It arises when an intruder crashes servers or create useless traffic to barren the access and denies service to the network.
3. Viruses and other Malicious Software: Unfortunately, some software and programs are specifically used or created with ill intention like:
**Viruses: It is a program that infects other files by creating a copy of itself.
**Worms: It is a program that propagates by sending copies of itself to other computers and there after again to others without the knowledge of the user.
**Trojan horses: It is a program that misleads the user by hiding its true intention and doing malicious activities in the background.
**Logic Bombs: It is a program that is intentionally inserted into a software to take its advantage (Often with ill intention) when certain conditions are met.
Network Designing:
Network designing is not an exact science but an iterative process that aims to ensure that the user's and project's requirements are fulfilled. It acts as a backbone of any IT business because it creates a network and connects all the network devices together allowing information access through out the industry. Before implementing any network design, it is planned to ensure its efficiency.
Any network design should show:
1. A clear map of the network.
2. Layout or wiring diagram of the cables.
3. The location, quantity and types of devices to be used.
4. Following a particular structure of IP Address.
5. Deciding network security architecture and processes.
To ensure the designed network is best following things are taken into account:
1. Actual design phase should be done diligently.
2. Always plan while keeping future in mind.
3. Security should be embedded in the design.
4. Network should be properly monitored.
5. Network designing never finishes.

